Your applications can connect to APIs in Google's production environment from within Google Cloud or from hybrid (on-premises and multicloud) networks. Google Cloud offers the following public and private access options, which offer global reachability and SSL/TLS security:
- Public internet access: Send traffic to
REGION-aiplatform.googleapis.com. - Private Google Access for on-premises hosts: Use the IP address
subnet range
199.36.153.8/30(private.googleapis.com) or199.36.153.4/30(restricted.googleapis.com) to accessREGION-aiplatform.googleapis.com. - Private Service Connect endpoints for Google APIs: Use a
user-defined internal IP address such as
10.0.0.100to accessREGION-aiplatform.googleapis.comor an assigned DNS name such asvertexai-genai1.p.googleapis.com.
The following diagram illustrates these access options.
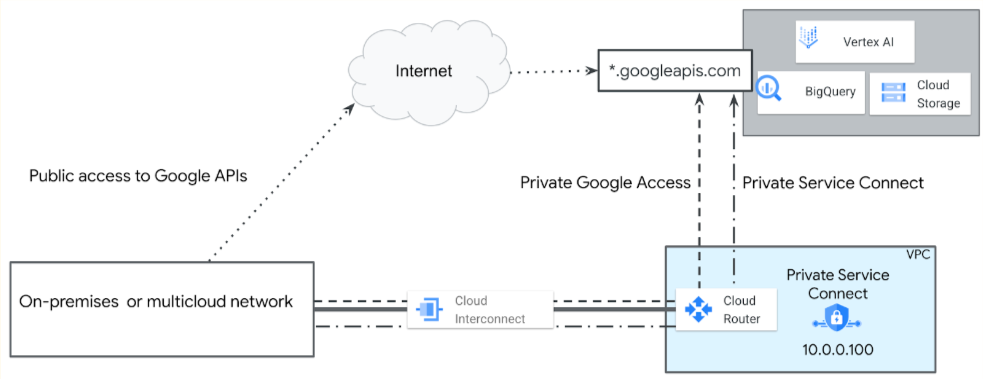
Some Vertex AI service producers require you to connect to their services through private services access or through Private Service Connect endpoints. These services are listed in the Private access options for Vertex AI table.
Public internet access to the Vertex AI API
If your application uses a Google service listed in the table of supported access methods for Vertex AI, your application can access the API by performing a DNS lookup against the
service endpoint
(REGION-aiplatform.googleapis.com), which returns
publicly routable virtual IP addresses. You can use the API from
any location in the world as long as you have an internet connection.
However, traffic that is sent from Google Cloud resources to those IP
addresses remains within Google's network.
Private access to the Vertex AI API
Private access is an alternative to connecting to Google APIs and services over the internet. It provides higher bandwidth, reliability and consistent performance. Google Cloud supports the following options for accessing Google APIs privately through hybrid networking services such as Cloud Interconnect, Cross-Cloud Interconnect, HA VPN over Cloud Interconnect, and SD-WAN.
Private Google Access for on-premises hosts
Private Google Access for on-premises hosts provides a way for on-premises systems to connect to Google APIs and services by routing traffic through hybrid networking services.
Private Google Access requires you to advertise one of the following subnet IP address ranges as a custom route advertisement by using Cloud Router:
private.googleapis.com:199.36.153.8/30,2600:2d00:0002:2000::/64restricted.googleapis.com:199.36.153.4/30,2600:2d00:0002:1000::/64
For more information, see Configure Private Google Access for on-premises hosts.
Private Service Connect endpoints for the Vertex AI API
With Private Service Connect, you can create private endpoints
using global internal IP addresses within your VPC network.
You can assign DNS names to these internal IP addresses with meaningful names
like vertexai-genai1.p.googleapis.com and
bigtable-adsteam.p.googleapis.com. These names and IP addresses are
internal to your VPC network and any on-premises networks
that are connected to it through hybrid networking services.
You can control which traffic goes to which endpoint, and can demonstrate
that traffic stays within Google Cloud.
- You can create a user-defined global Private Service Connect endpoint IP address (/32). For more information, see IP address requirements.
- You create the Private Service Connect endpoint in the same VPC network as the Cloud Router.
- You can assign DNS names to these internal IP addresses with meaningful
names like
aiplatform-prodpsc.p.googleapis.com. For more information, see About accessing Google APIs through endpoints.
Deployment considerations
Following are some important considerations that affect how you use Private Google Access and Private Service Connect to access the Vertex AI API.
IP advertisement
You must advertise the Private Google Access subnet range or the Private Service Connect endpoint IP address to on-premises and multicloud environments from the Cloud Router as a custom route advertisement. For more information, see Advertise custom IP ranges.
Firewall rules
You must ensure that the firewall configuration of on-premises and multicloud environments allows outbound traffic from the IP addresses of Private Google Access or Private Service Connect subnets.
DNS configuration
- Your on-premises network must have DNS zones and records configured so that
a request to
REGION-aiplatform.googleapis.comresolves to the Private Google Access subnet or the Private Service Connect endpoint IP address. - You can create Cloud DNS managed private zones and use a Cloud DNS inbound server policy, or you can configure on-premises name servers. For example, you can use BIND or Microsoft Active Directory DNS.
- If your on-premises network is connected to a VPC network, you can use Private Service Connect to access Google APIs and services from on-premises hosts using the internal IP address of the endpoint. For more information, see Access the endpoint from on-premises hosts.
